Fun with WiFi: SSID-Overload!
For this post we will be looking at how the WiFi protocol (IEEE 802.11) allows alien devices to view network paramaters prior to connecting, and also looking at how we can advertise our own networks in this manner.
To begin with, 802.11 Beacon Frames are by default sent out by all access-points every 102.4 millseconds, or ~ 0.1 seconds, and these are what allow your iPhone to see nearby networks. Beacons contain all sorts of juicy information advertising the wireless network parameters to potential clients, and to synchronise access-points in an Exended-Service-Set WLAN.
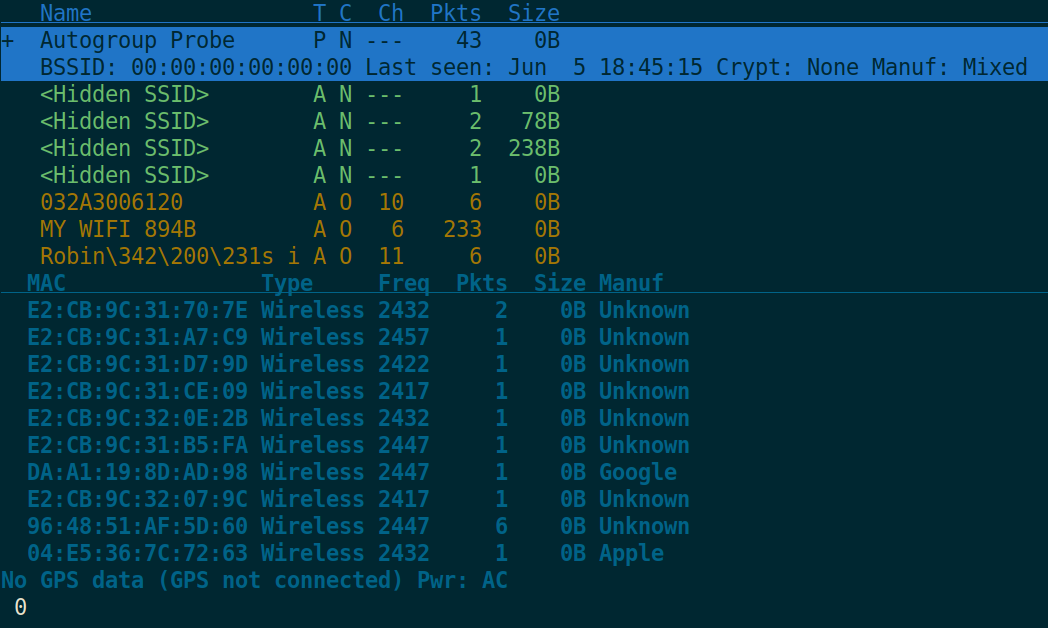
Wireless devices, even when not connected to a network, will send regular probe requests to broadcast address 00:00:00:00:00:00, begging for connection parameters. We can see this is the below "Autogroup Probe" group:
In order to see these signalling messages at all, we must first set our wireless interface into monitor mode. This is commonly refered to as "promiscuous" mode, because our WiFi NIC will be ready to chat to literally anybody. We can do this traditionally by shutting down our interface and using the iwconfig tool, or the highly popular Aircrack-NG (next-generation) suite has a tool to automate the process for us:
sudo ip link set wlan1 down
sudo iwconfig wlan1 mode monitor
sudo ip link set wlan1 up
And using Airmon-NG:
sudo airmon-ng start wlan1
Note that Airmon-NG will create a brand new virtual interface named mon0.
Now that our adapter is ready to talk the talk, we can use the MDK3 (Murder-Death-Kill...ikr) tool to craft our own Beacon frames. In beacon mode, this tool can be set to read ESSID names from a text file, which is always fun:
cat << EOF > essidnames
This is a network
This is a network too
I am also a network
Network over here, yo
Oh shit waddup, its dat network
Network checking in
This is most definitely a network
EOF
The above can be accomplished with literally any text editor, but I'm just obessed with my recent Cat-To-HereDoc find.
With our wordlist prepared, let's initialize and put MDK3 to the test:
sudo mdk3 mon0 b -f essidnames
And the results...
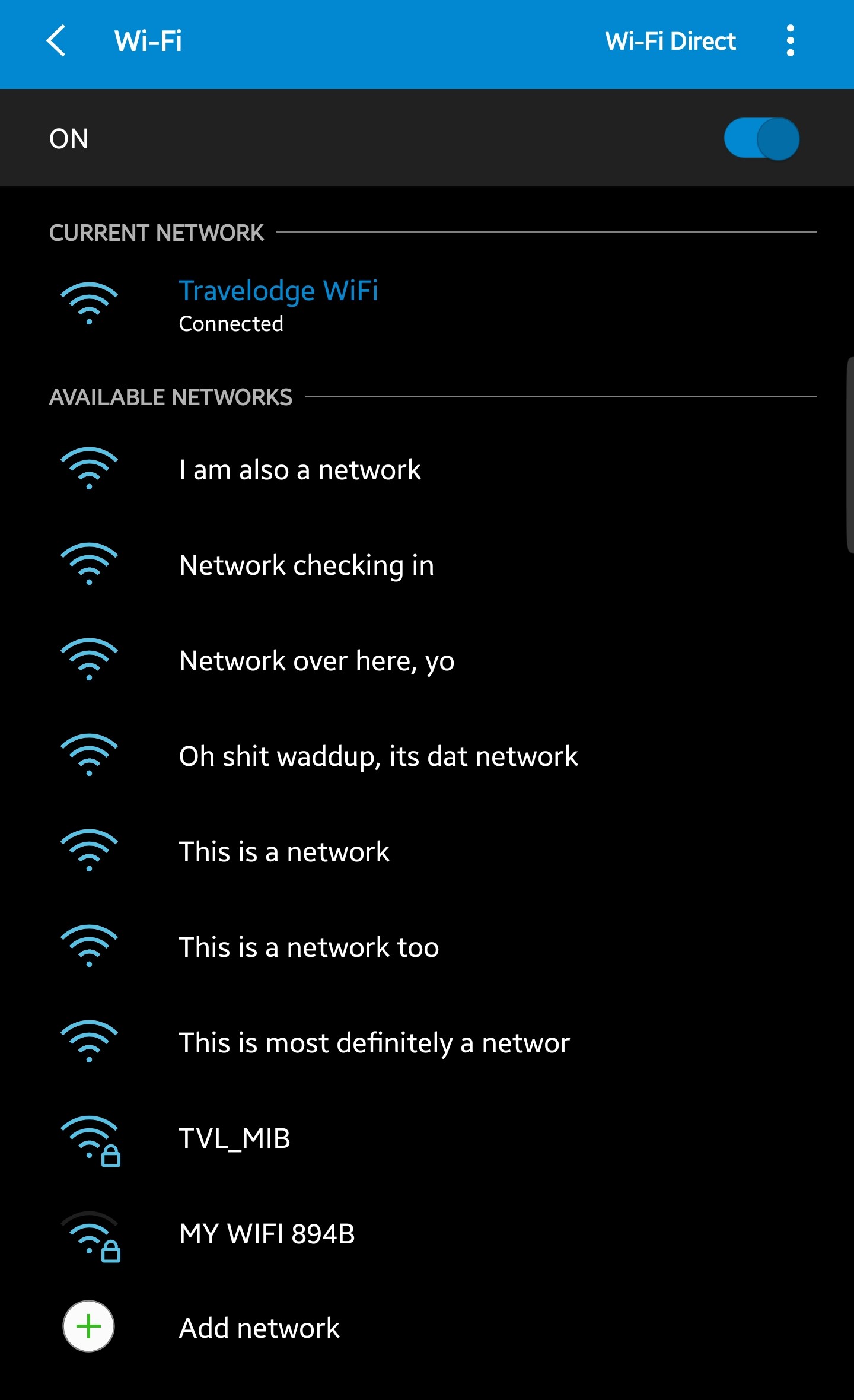
Hoorah!
This is a quick look at beacon frames, and I will be moving onto some fun stuff in the near future.
Thanks for reading along!
